 Anybody care to speculate on the outcome? There is a good chance that Tim Cook may end up like LaVoy Fenicum. — jtl, 419
Anybody care to speculate on the outcome? There is a good chance that Tim Cook may end up like LaVoy Fenicum. — jtl, 419A tech giant draws a line in the sand
Too often, corporations serve as quiet collaborators for the surveillance state to avoid retribution from the government. On Tuesday, Apple CEO Tim Cook provided a rare and extraordinary exception to this unfortunate trend in the tech industry by publicly resisting a court order to compromise iPhone security.  Since the horrific San Bernardino attacks late last year, the FBI has been seeking access to communications in an iPhone 5c used by the deceased shooter Syed Rizwan Farook. The problem? Agents could not actually access the data without the user PIN needed to unlock the screen. Farook obviously cannot provide the PIN, and just ten false guesses would trigger a security feature that wipes the phone’s memory.
Since the horrific San Bernardino attacks late last year, the FBI has been seeking access to communications in an iPhone 5c used by the deceased shooter Syed Rizwan Farook. The problem? Agents could not actually access the data without the user PIN needed to unlock the screen. Farook obviously cannot provide the PIN, and just ten false guesses would trigger a security feature that wipes the phone’s memory.
 So the g-men dusted off the All Writs Act of 1789 and called in some judicial muscle. The FBI sought and got a court order from Magistrate Judge Sheri Pym compelling Apple to “provide reasonable technical assistance” to grant law enforcement access to the phone.
So the g-men dusted off the All Writs Act of 1789 and called in some judicial muscle. The FBI sought and got a court order from Magistrate Judge Sheri Pym compelling Apple to “provide reasonable technical assistance” to grant law enforcement access to the phone.
Sounds reasonable enough, right? There’s a straightforward target and a real investigation. Cook points out that Apple has already provided considerable data and assistance for this investigation in other capacities. Unlike some other law enforcement proposals to evade encryption, the technical method that the  FBI now desires could be workable and probably inexpensive. All that iPhone engineers would have to do is create a program that would allow the government to try an unlimited number of PIN combinations in quick succession and roll out the feature in the next iOS update.
FBI now desires could be workable and probably inexpensive. All that iPhone engineers would have to do is create a program that would allow the government to try an unlimited number of PIN combinations in quick succession and roll out the feature in the next iOS update.
In other words, Judge Pym and the FBI want Apple to build a government backdoor into their operating system. If instituted, this technique would potentially allow federal agents to access not only the iPhone that Farook used, but also the device that is likely in your pocket right now. Additionally, this action would create  a dangerous and high-profile precedent for compelling backdoors in systems that smaller fish than Apple would find hard to resist.
a dangerous and high-profile precedent for compelling backdoors in systems that smaller fish than Apple would find hard to resist.
What the FBI requested was nothing short of a revolutionary assault on digital privacy and security, based on an exceedingly broad interpretation of a centuries-old relic. If Apple complied, the effects on our freedoms of speech and privacy could be catastrophic.
 On this point, Cook did not mince words. He writes:
On this point, Cook did not mince words. He writes:
The implications of the government’s demands are chilling. If the government can use the All Writs Act to make it easier to unlock your iPhone, it would have the power to reach into anyone’s device to capture their data.
The government could extend this breach of privacy and demand that Apple build surveillance software to intercept your messages, access your health records or financial data, track your location, or even access your phone’s microphone or camera without your knowledge.
Chilling, indeed.
I believe Cook when he says his company is not opposing this order lightly. Defying the US surveillance state is no cakewalk, even for one of the richest and most respected companies in the world. Indeed, it’s worth reflecting on the state of affairs in which only the most powerful corporations have the means and support to openly resist government intrusion. Even worse, the organizations most able to resist creeping tyranny are often also the ones that primarily benefit from its uninterrupted advance.
Cook’s public stand serves as a welcome broadside against law enforcement’s years-long jihad against strong encryption technologies. Recently, a group of political leaders have sought ways to allow instant government access to “encrypted” communications that are concealed from unwanted eyes through special mathematical techniques. The War on Terror has only amplified their frenzied crusade.
Apple’s defiance also makes good business sense: government backdoors create massive security vulnerabilities that savvy companies smartly and emphatically oppose. Apple is in the business of selling good products that look nice and stay secure. The prospect of allowing ham-handed security holes for federal agents — who craft passwords like “Pass1234” and grant Chinese hackers root access to federal databases — surely strikes terror in the hearts of corporate attorneys and IT experts.
If there’s one thing Apple excels at, it’s making money. Handing over the integrity of a core profit-generator to cartoonishly inept bureaucrats is not part of that plan.
Ironically, these kinds of power grabs may end up pushing device manufacturers to make more products that are impenetrable to government backdoors by design. (For the record, Tim, I would be an enthusiastic early adopter!) Apple could design their software and products in such a way that they could not divulge customer information, even if they wanted to. Without a trusted third party to pressure, that security hole will cease to exist. In the long run, such a strategy is perhaps one of the only surefire ways to fully thwart government meddling in information security.
Let’s give three cheers for Apple’s strong stand against government backdoors. May their example inspire others to develop protections against state encroachments on our data.
 All unclassified Army and Marine Cops manuals and correspondence courses are products of the US Federal Government. They are NOT subject to copyright and can be freely copied and redistributed.
All unclassified Army and Marine Cops manuals and correspondence courses are products of the US Federal Government. They are NOT subject to copyright and can be freely copied and redistributed.
The Marine Corps Institute (MCI) develops correspondence courses for Marines with all kinds of Military Occupational Specialties (MOS) on all manner of subjects. This is one of those courses.
The print is relatively small because that is the way it was in the original and this is an exact reproduction. Also, as a tribute to the individual (and a touch of reality), you will notice that the editorial pencil marks and underlined passages that were put there by the Marine that took this course. They were intentionally left in the reproduction.
This version of the course was authorized in September of 1984. With the exception the development of Infrared technology, it contains information and techniques that have changed very little since the Vietnam war. These battle proven tactics are as valid today as they were in Quang Nam province in 1968.
They will maintain their validity during the upcoming inevitable event of total economic, political and social collapse. Yours for freedom in our lifetimes. jtl, 419




 24 Hour Spot Gold Prices
24 Hour Spot Gold Prices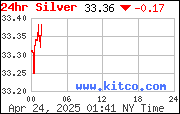 24 Hour Spot Silver Prices
24 Hour Spot Silver Prices A Handbook for Ranch Managers
A Handbook for Ranch Managers Combat Shooter's Handbook
Combat Shooter's Handbook Flyover Store
Flyover Store FlyoverPress on the Web
FlyoverPress on the Web Planned Grazing: A Study Guide and Reference Manual
Planned Grazing: A Study Guide and Reference Manual The Betrayed: On Warriors, Cowboys and Other Misfits
The Betrayed: On Warriors, Cowboys and Other Misfits